“Securing Google Cloud with CFT Scorecard”
Daftar Isi
Pengantar
CFT Scorecard adalah klien baris perintah sumber terbuka dari Forseti Config Validator dan bagian dari Cloud Foundation Toolkit yang lebih luas. Ini memberikan visibilitas ke kesalahan konfigurasi dan pelanggaran terhadap serangkaian standar yang ditetapkan untuk resource, project, folder, atau bahkan organisasi Google Cloud.
Ada lebih dari 86 jenis resource Google Cloud yang berbeda, dan terus bertambah. Dengan perpindahan ke cloud publik, semakin mudah untuk menyatukan operasi cloud dan penyebaran sumber daya ke banyak individu. Seiring dengan federasi dan ketangkasan dalam penyebaran infrastruktur, sumber daya, dan kebijakan, semakin sulit untuk menjaga agar kebijakan dan standar tetap teratur.
Architecture
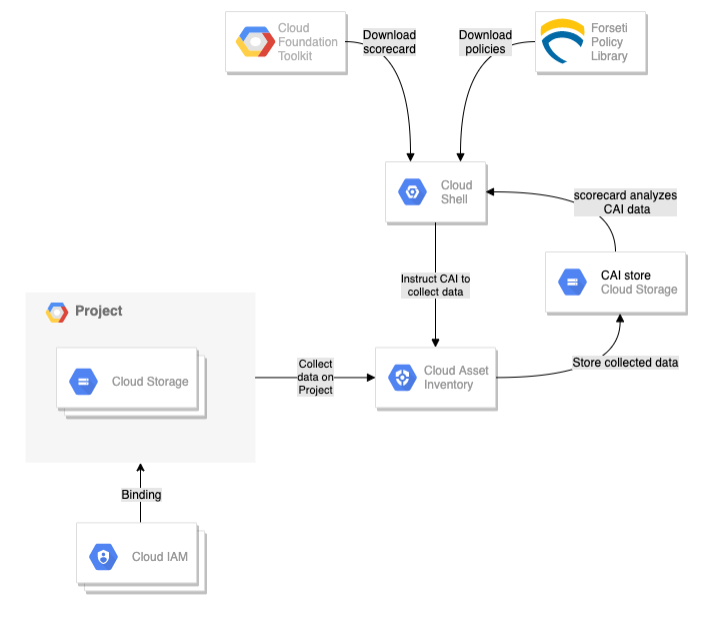
Praktikum
Task 1. Set up the environment
- Open Cloud Shell and set a couple of environment variables to begin:
export GOOGLE_PROJECT=$DEVSHELL_PROJECT_ID
export CAI_BUCKET_NAME=cai-$GOOGLE_PROJECT
gcloud services enable cloudasset.googleapis.com \
--project $GOOGLE_PROJECT
gcloud beta services identity create --service=cloudasset.googleapis.com --project=$GOOGLE_PROJECTgcloud projects add-iam-policy-binding ${GOOGLE_PROJECT} \
--member=serviceAccount:service-$(gcloud projects list --filter="$GOOGLE_PROJECT" --format="value(PROJECT_NUMBER)")@gcp-sa-cloudasset.iam.gserviceaccount.com \
--role=roles/storage.admin- Clone Policy
git clone https://github.com/forseti-security/policy-library.git- You realize Policy Library enforces policies that are located in the policy-library/policies/constraints folder, in which case you can copy a sample policy from the samples directory into the constraints directory.
cp policy-library/samples/storage_denylist_public.yaml policy-library/policies/constraints/- Create the bucket that will hold the data that Cloud Asset Inventory (CAI) will export:
gsutil mb -l us-central1 -p $GOOGLE_PROJECT gs://$CAI_BUCKET_NAMETask 2. Collect data using Cloud Asset Inventory (CAI)
- Use the command below to create the data:
# Export resource data
gcloud asset export \
--output-path=gs://$CAI_BUCKET_NAME/resource_inventory.json \
--content-type=resource \
--project=$GOOGLE_PROJECT
# Export IAM data
gcloud asset export \
--output-path=gs://$CAI_BUCKET_NAME/iam_inventory.json \
--content-type=iam-policy \
--project=$GOOGLE_PROJECT
# Export org policy data
gcloud asset export \
--output-path=gs://$CAI_BUCKET_NAME/org_policy_inventory.json \
--content-type=org-policy \
--project=$GOOGLE_PROJECT
# Export access policy data
gcloud asset export \
--output-path=gs://$CAI_BUCKET_NAME/access_policy_inventory.json \
--content-type=access-policy \
--project=$GOOGLE_PROJECTTask 3. Analyze CAI data with CFT scorecard
- You need to download the CFT scorecard application and make it executable:
curl -o cft https://storage.googleapis.com/cft-cli/latest/cft-linux-amd64
# make executable
chmod +x cft- Now that you have configured everything, go ahead and run the CFT scorecard application:
./cft scorecard --policy-path=policy-library/ --bucket=$CAI_BUCKET_NAMETask 4. Add more constraints to CFT scorecard
- You forgot about IAM! Add the following constraint to ensure you are entirely aware who has the
roles/ownerrole aside from your allowlisted user:
# Add a new policy to blacklist the IAM Owner Role
cat > policy-library/policies/constraints/iam_allowlist_owner.yaml << EOF
apiVersion: constraints.gatekeeper.sh/v1alpha1
kind: GCPIAMAllowedBindingsConstraintV3
metadata:
name: allowlist_owner
annotations:
description: List any users granted Owner
spec:
severity: high
match:
target: ["organizations/**"]
exclude: []
parameters:
mode: allowlist
assetType: cloudresourcemanager.googleapis.com/Project
role: roles/owner
members:
- "serviceAccount:[email protected]"
EOF- Rerun CFT scorecard:
./cft scorecard --policy-path=policy-library/ --bucket=$CAI_BUCKET_NAME- Set two extra variables to help with the new constraint creation:
export USER_ACCOUNT="$(gcloud config get-value core/account)"
export PROJECT_NUMBER=$(gcloud projects describe $GOOGLE_PROJECT --format="get(projectNumber)")- Create the following constraint that will allowlist all the valid accounts:
# Add a new policy to allowlist the IAM Editor Role
cat > policy-library/policies/constraints/iam_identify_outside_editors.yaml << EOF
apiVersion: constraints.gatekeeper.sh/v1alpha1
kind: GCPIAMAllowedBindingsConstraintV3
metadata:
name: identify_outside_editors
annotations:
description: list any users outside the organization granted Editor
spec:
severity: high
match:
target: ["organizations/**"]
exclude: []
parameters:
mode: allowlist
assetType: cloudresourcemanager.googleapis.com/Project
role: roles/editor
members:
- "user:$USER_ACCOUNT"
- "serviceAccount:**$PROJECT_NUMBER**gserviceaccount.com"
- "serviceAccount:$GOOGLE_PROJECT**gserviceaccount.com"
EOF- Rerun CFT scorecard:
./cft scorecard --policy-path=policy-library/ --bucket=$CAI_BUCKET_NAMEPenutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Securing Google Cloud with CFT Scorecard. Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.














