“Building a High-throughput VPN”
Daftar Isi
Pengantar
Komunikasi yang aman antara Google Cloud dan cloud lain atau sistem lokal adalah kebutuhan umum yang sangat penting. Untungnya, Google Cloud memudahkan Anda membuat jaringan pribadi virtual (VPN) keamanan Protokol Internet (IPsec) yang aman untuk mencapai tujuan ini. Jika satu tunnel tidak menyediakan throughput yang diperlukan, Google Cloud dapat mendistribusikan traffic dengan lancar ke beberapa tunnel untuk menyediakan bandwidth tambahan.
Buat Cloud VPC
- Buat VPC namanya cloud
gcloud compute networks create cloud --subnet-mode custom
- Buat frewall untuk VPC cloud
gcloud compute firewall-rules create cloud-fw --network cloud --allow tcp:22,tcp:5001,udp:5001,icmp
- Buat Subnet
gcloud compute networks subnets create cloud-east --network cloud \
--range 10.0.1.0/24 --region us-east1
Buat on-prem VPC
- Buat VPC namanya
on-prem
gcloud compute networks create on-prem --subnet-mode custom
gcloud compute firewall-rules create on-prem-fw --network on-prem --allow tcp:22,tcp:5001,udp:5001,icmp
- Buat Subnet
gcloud compute networks subnets create on-prem-central \
--network on-prem --range 192.168.1.0/24 --region us-central1
Buat VPN gateways
- Buat Gateway
on-prem-gw1untuk VPCon-prem
gcloud compute target-vpn-gateways create on-prem-gw1 --network on-prem --region us-central1
- Buat Gateway
cloud-gw1untuk VPC cloud
gcloud compute target-vpn-gateways create cloud-gw1 --network cloud --region us-east1
Buat route-based VPN tunnel antara loca dan Google Cloud networks
- Buat Alokasi IP untuk
cloud-gw1VPN gateway
gcloud compute addresses create cloud-gw1 --region us-east1
- Buat Alokasi IP untuk
on-prem-gw1VPN gateway
gcloud compute addresses create on-prem-gw1 --region us-central1
- Store gateway
cloud-gw1
cloud_gw1_ip=$(gcloud compute addresses describe cloud-gw1 \
--region us-east1 --format='value(address)')
- Store gateway
on-prem-gw1
on_prem_gw_ip=$(gcloud compute addresses describe on-prem-gw1 \
--region us-central1 --format='value(address)')
- Forward Encapsulating Security Payload (ESP) protocol dari
cloud-gw1
gcloud compute forwarding-rules create cloud-1-fr-esp --ip-protocol ESP \
--address $cloud_gw1_ip --target-vpn-gateway cloud-gw1 --region us-east1
- Forward
UDP:500traffic dari cloud-gw1
gcloud compute forwarding-rules create cloud-1-fr-udp500 --ip-protocol UDP \
--ports 500 --address $cloud_gw1_ip --target-vpn-gateway cloud-gw1 --region us-east1
- Forward
UDP:4500traffic dari cloud-gw1
gcloud compute forwarding-rules create cloud-fr-1-udp4500 --ip-protocol UDP \
--ports 4500 --address $cloud_gw1_ip --target-vpn-gateway cloud-gw1 --region us-east1
- Forward ESP protocol dari
on-prem-gw1
gcloud compute forwarding-rules create on-prem-fr-esp --ip-protocol ESP \
--address $on_prem_gw_ip --target-vpn-gateway on-prem-gw1 --region us-central1
- Forward
UDP:500
gcloud compute forwarding-rules create on-prem-fr-udp500 --ip-protocol UDP --ports 500 \
--address $on_prem_gw_ip --target-vpn-gateway on-prem-gw1 --region us-central1
- Forward
UDP:4500
gcloud compute forwarding-rules create on-prem-fr-udp4500 --ip-protocol UDP --ports 4500 \
--address $on_prem_gw_ip --target-vpn-gateway on-prem-gw1 --region us-central1
- Buat VPN tunnel dari
on-premkecloud
gcloud compute vpn-tunnels create on-prem-tunnel1 --peer-address $cloud_gw1_ip \
--target-vpn-gateway on-prem-gw1 --ike-version 2 --local-traffic-selector 0.0.0.0/0 \
--remote-traffic-selector 0.0.0.0/0 --shared-secret=[MY_SECRET] --region us-central1
- Buat VPN tunnel dari cloud ke on-prem
gcloud compute vpn-tunnels create cloud-tunnel1 --peer-address $on_prem_gw_ip \
--target-vpn-gateway cloud-gw1 --ike-version 2 --local-traffic-selector 0.0.0.0/0 \
--remote-traffic-selector 0.0.0.0/0 --shared-secret=[MY_SECRET] --region us-east1
- Route traffic dari
on-premVPC kecloud 10.0.1.0/24range kedalam tunnel
gcloud compute routes create on-prem-route1 --destination-range 10.0.1.0/24 \
--network on-prem --next-hop-vpn-tunnel on-prem-tunnel1 \
--next-hop-vpn-tunnel-region us-central1
- Route traffic dari
cloudVPC keon-prem 192.168.1.0/24range kedalam tunnel
gcloud compute routes create cloud-route1 --destination-range 192.168.1.0/24 \
--network cloud --next-hop-vpn-tunnel cloud-tunnel1 --next-hop-vpn-tunnel-region us-east1
Testing throughput Dari VPN
Single VPN load testing
- Buat VM
cloud-loadtestuntuk cloud VPC
gcloud compute instances create "cloud-loadtest" --zone "us-east1-b" \
--machine-type "n1-standard-4" --subnet "cloud-east" \
--image "debian-9-stretch-v20180814" --image-project "debian-cloud" --boot-disk-size "10" \
--boot-disk-type "pd-standard" --boot-disk-device-name "cloud-loadtest"
- Buat VM
on-prem-loadtestuntuk on-prem VPC
gcloud compute instances create "on-prem-loadtest" --zone "us-central1-a" \
--machine-type "n1-standard-4" --subnet "on-prem-central" \
--image "debian-9-stretch-v20180814" --image-project "debian-cloud" --boot-disk-size "10" \
--boot-disk-type "pd-standard" --boot-disk-device-name "on-prem-loadtest"
sudo apt-get install iperf
- Pada VM
on-prem-loadtest, jalankan perintah berikut
iperf -s -i 5
- Pada Vm
cloud-loadtest, jalankan perintah berikut
iperf -c 192.168.1.2 -P 20 -x C
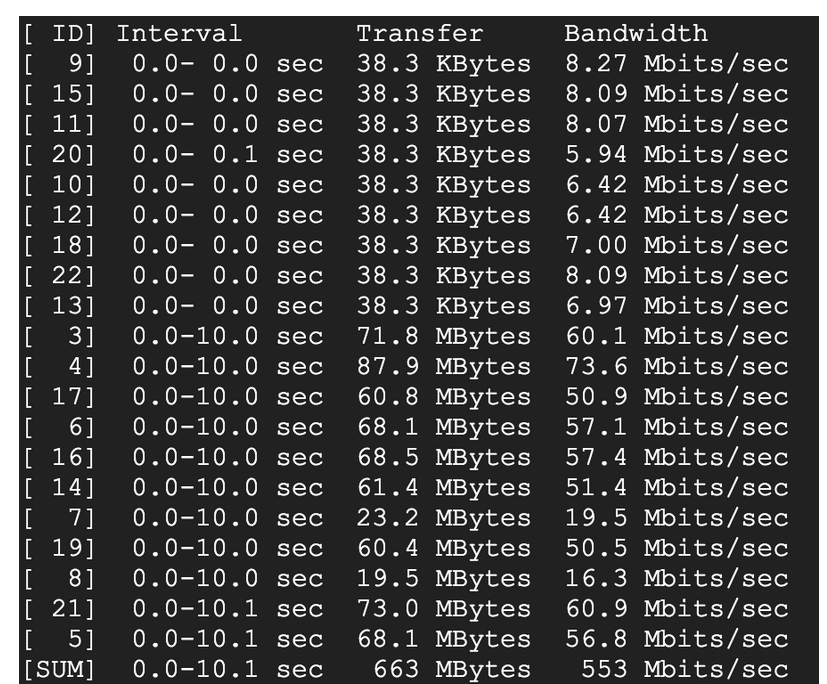
Penutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Building a High-throughput VPN. Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.














