“Google Cloud Packet Mirroring with OpenSource IDS”
Daftar Isi
Pengantar
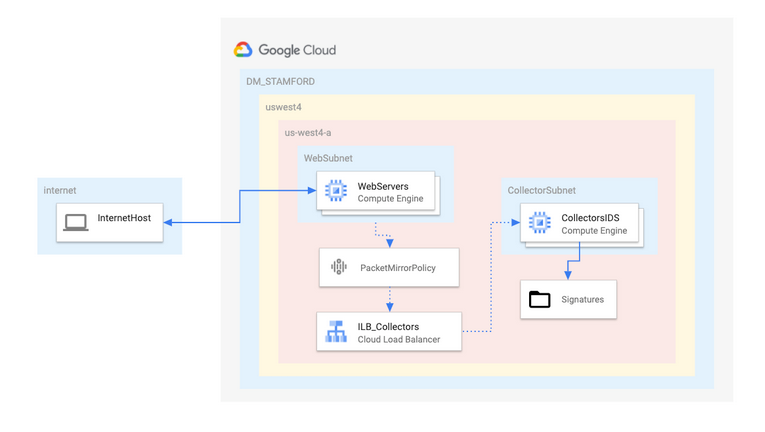
Traffic Mirroring adalah fitur utama dalam jaringan Google Cloud untuk keamanan dan analisis jaringan. Fungsionalitasnya mirip dengan ketukan jaringan atau sesi rentang dalam jaringan tradisional. Singkatnya, Pencerminan Paket menangkap lalu lintas jaringan (masuk dan keluar) dari “sumber cermin” tertentu, menyalin lalu lintas, dan meneruskan salinan ke “pengumpul”.
Penting untuk dicatat bahwa Pencerminan Paket menangkap muatan penuh dari setiap paket dan dengan demikian menghabiskan bandwidth tambahan. Karena Packet Mirroring tidak didasarkan pada periode pengambilan sampel apa pun, itu dapat digunakan untuk pemecahan masalah yang lebih baik, solusi keamanan, dan analisis berbasis aplikasi lapisan yang lebih tinggi.
Architecture
Praktikum
Task 1. Build a networking footprint
- Run the following to create a virtual private network:
gcloud compute networks create dm-stamford \
--subnet-mode=custom- Add a subnet to the VPC for mirrored traffic in us-west4:
gcloud compute networks subnets create dm-stamford-uswest4 \
--range=172.21.0.0/24 \
--network=dm-stamford \
--region=us-west4- Add a subnet to the VPC for the collector in us-west4:
gcloud compute networks subnets create dm-stamford-uswest4-ids \
--range=172.21.1.0/24 \
--network=dm-stamford \
--region=us-west4Task 2. Create firewall rules and Cloud NAT
- Run the following commands to create the firewall rules:
gcloud compute firewall-rules create fw-dm-stamford-allow-any-web \
--direction=INGRESS \
--priority=1000 \
--network=dm-stamford \
--action=ALLOW \
--rules=tcp:80,icmp \
--source-ranges=0.0.0.0/0gcloud compute firewall-rules create fw-dm-stamford-ids-any-any \
--direction=INGRESS \
--priority=1000 \
--network=dm-stamford \
--action=ALLOW \
--rules=all \
--source-ranges=0.0.0.0/0 \
--target-tags=idsgcloud compute firewall-rules create fw-dm-stamford-iapproxy \
--direction=INGRESS \
--priority=1000 \
--network=dm-stamford \
--action=ALLOW \
--rules=tcp:22,icmp \
--source-ranges=35.235.240.0/20Create a Cloud Router
gcloud compute routers create router-stamford-nat-west4 \
--region=us-west4 \
--network=dm-stamfordConfigure a Cloud NAT
gcloud compute routers nats create nat-gw-dm-stamford-west4 \
--router=router-stamford-nat-west4 \
--router-region=us-west4 \
--auto-allocate-nat-external-ips \
--nat-all-subnet-ip-rangesTask 3. Create virtual machines
Create an instance template for a web server
gcloud compute instance-templates create template-dm-stamford-web-us-west4 \
--region=us-west4 \
--network=dm-stamford \
--subnet=dm-stamford-uswest4 \
--machine-type=g1-small \
--image=ubuntu-1604-xenial-v20200807 \
--image-project=ubuntu-os-cloud \
--tags=webserver \
--metadata=startup-script='#! /bin/bash
apt-get update
apt-get install apache2 -y
vm_hostname="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/name)"
echo "Page served from: $vm_hostname" | \
tee /var/www/html/index.html
systemctl restart apache2'Create a managed instance group for the web servers
gcloud compute instance-groups managed create mig-dm-stamford-web-uswest4 \
--template=template-dm-stamford-web-us-west4 \
--size=2 \
--zone=us-west4-aCreate an Instance Template for the IDS VM
gcloud compute instance-templates create template-dm-stamford-ids-us-west4 \
--region=us-west4 \
--network=dm-stamford \
--no-address \
--subnet=dm-stamford-uswest4-ids \
--image=ubuntu-1604-xenial-v20200807 \
--image-project=ubuntu-os-cloud \
--tags=ids,webserver \
--metadata=startup-script='#! /bin/bash
apt-get update
apt-get install apache2 -y
vm_hostname="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/name)"
echo "Page served from: $vm_hostname" | \
tee /var/www/html/index.html
systemctl restart apache2'Create a managed instance group for the IDS VM
gcloud compute instance-groups managed create mig-dm-stamford-ids-uswest4 \
--template=template-dm-stamford-ids-us-west4 \
--size=1 \
--zone=us-west4-aTask 4. Create an internal load balancer
- Create a basic health check for the backend services:
gcloud compute health-checks create tcp hc-tcp-80 --port 80- Create a backend service group to be used for an ILB:
gcloud compute backend-services create be-dm-stamford-suricata-us-west4 \
--load-balancing-scheme=INTERNAL \
--health-checks=hc-tcp-80 \
--network=dm-stamford \
--protocol=TCP \
--region=us-west4- Add the created IDS managed instance group into the backend service group created in the previous step:
gcloud compute backend-services add-backend be-dm-stamford-suricata-us-west4 \
--instance-group=mig-dm-stamford-ids-uswest4 \
--instance-group-zone=us-west4-a \
--region=us-west4- Create a front end forwarding rule to act as the collection endpoint:
gcloud compute forwarding-rules create ilb-dm-stamford-suricata-ilb-us-west4 \
--load-balancing-scheme=INTERNAL \
--backend-service be-dm-stamford-suricata-us-west4 \
--is-mirroring-collector \
--network=dm-stamford \
--region=us-west4 \
--subnet=dm-stamford-uswest4-ids \
--ip-protocol=TCP \
--ports=allTask 5. Install open source IDS – Suricata
SSH into the IDS VM
- Using the Cloud Console, from the Navigation menu, navigate to Compute Engine > VM Instances.
- Click on the SSH button of your IDS VM.
- Update the IDS VM:
sudo apt-get update -y- Install Suricata dependencies:
sudo apt-get install libpcre3-dbg libpcre3-dev autoconf automake libtool libpcap-dev libnet1-dev libyaml-dev zlib1g-dev libcap-ng-dev libmagic-dev libjansson-dev libjansson4 -ysudo apt-get install libnspr4-dev -y
sudo apt-get install libnss3-dev -y
sudo apt-get install liblz4-dev -y
sudo apt install rustc cargo -y- Install Suricata:
sudo add-apt-repository ppa:oisf/suricata-stable -y
sudo apt-get update -y
sudo apt-get install suricata -y- Cek Versi
suricata -VTask 6. Configure and review Suricata
- Stop the Suricata service and backup the default configuration file:
sudo systemctl stop suricata
sudo cp /etc/suricata/suricata.yaml /etc/suricata/suricata.backupDownload and replace new Suricata configuration file and abridged rules file
- Run the following commands to copy the files.
wget https://storage.googleapis.com/tech-academy-enablement/GCP-Packet-Mirroring-with-OpenSource-IDS/suricata.yaml
wget https://storage.googleapis.com/tech-academy-enablement/GCP-Packet-Mirroring-with-OpenSource-IDS/my.rules
sudo mkdir /etc/suricata/poc-rules
sudo cp my.rules /etc/suricata/poc-rules/my.rules
sudo cp suricata.yaml /etc/suricata/suricata.yamlStart the Suricata service
sudo systemctl start suricata
sudo systemctl restart suricataTask 7. Configure Packet Mirror policy
- Configure Packet Mirroring Policy by running the following in Cloud Shell:
gcloud compute packet-mirrorings create mirror-dm-stamford-web \
--collector-ilb=ilb-dm-stamford-suricata-ilb-us-west4 \
--network=dm-stamford \
--mirrored-subnets=dm-stamford-uswest4 \
--region=us-west4Task 8. Test Packet Mirroring
gcloud compute instances list
sudo tcpdump -i ens4 -nn -n "(icmp or port 80) and net 172.21.0.0/24"Generate traffic to the “mirrored” subnet
sudo apt install iputils-ping
ping -c 4 [PUBLIC_IP_WEB1]
ping -c 4 [PUBLIC_IP_WEB2]Task 9. Test Suricata IDS inspection and alerts
dig @8.8.8.8 example.com
egrep "BAD UDP DNS" /var/log/suricata/eve.json
telnet 100.64.1.1 6667
egrep "BAD TCP" /var/log/suricata/eve.json
ping -c 3 [PUBLIC_IP_WEB1]
egrep "BAD ICMP" /var/log/suricata/eve.json
http://[PUBLIC_IP_WEB1]/index.php
egrep "BAD HTTP" /var/log/suricata/eve.jsonPenutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Google Cloud Packet Mirroring with OpenSource IDS. Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.