“Cloud KMS”
Daftar Isi
Pengantar
Cloud KMS adalah layanan pengelolaan kunci kriptografi di Google Cloud. Sebelum menggunakan KMS, Anda harus mengaktifkannya di proyek Anda. Di lab ini Anda telah disediakan KMS yang seharusnya sudah diaktifkan. Anda dapat memastikannya dengan menggunakan salah satu perintah gcloud CLI. Jalankan yang berikut ini di sesi Cloud Shell Anda:
Buat Cloud Storage bucket
- Jalankan cloud shell berikut
BUCKET_NAME=<YOUR_NAME>_enron_corpus
- Buat Bucket
gsutil mb gs://${BUCKET_NAME}
Check out the data
gsutil cp gs://enron_emails/allen-p/inbox/1. .
- tail download
tail 1.
Enable Cloud KMS
gcloud services enable cloudkms.googleapis.com
Buat Keyring dan Cryptokey
KEYRING_NAME=test CRYPTOKEY_NAME=qwiklab
- Buat keyring
gcloud kms keyrings create $KEYRING_NAME --location global
- Buat cryptokey
gcloud kms keys create $CRYPTOKEY_NAME --location global \
--keyring $KEYRING_NAME \
--purpose encryption
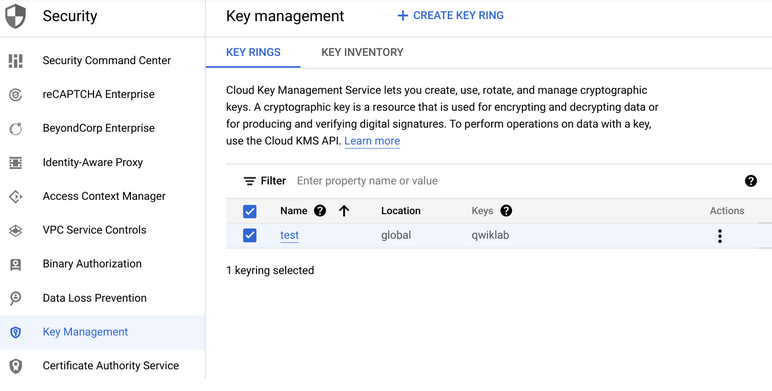
- Buka Navigation menu > Security > Key management:
Encrypt Your Data
PLAINTEXT=$(cat 1. | base64 -w0)
- encrypt key
curl -v "https://cloudkms.googleapis.com/v1/projects/$DEVSHELL_PROJECT_ID/locations/global/keyRings/$KEYRING_NAME/cryptoKeys/$CRYPTOKEY_NAME:encrypt" \ -d "{\"plaintext\":\"$PLAINTEXT\"}" \ -H "Authorization:Bearer $(gcloud auth application-default print-access-token)"\ -H "Content-Type: application/json"
- save file
curl -v "https://cloudkms.googleapis.com/v1/projects/$DEVSHELL_PROJECT_ID/locations/global/keyRings/$KEYRING_NAME/cryptoKeys/$CRYPTOKEY_NAME:encrypt" \
-d "{\"plaintext\":\"$PLAINTEXT\"}" \
-H "Authorization:Bearer $(gcloud auth application-default print-access-token)"\
-H "Content-Type:application/json" \
| jq .ciphertext -r > 1.encrypted
- cek decrypt
curl -v "https://cloudkms.googleapis.com/v1/projects/$DEVSHELL_PROJECT_ID/locations/global/keyRings/$KEYRING_NAME/cryptoKeys/$CRYPTOKEY_NAME:decrypt" \
-d "{\"ciphertext\":\"$(cat 1.encrypted)\"}" \
-H "Authorization:Bearer $(gcloud auth application-default print-access-token)"\
-H "Content-Type:application/json" \
| jq .plaintext -r | base64 -d
- upload encrypt file ke bucket
gsutil cp 1.encrypted gs://${BUCKET_NAME}
Configure IAM Permissions
- authorize user
USER_EMAIL=$(gcloud auth list --limit=1 2>/dev/null | grep '@' | awk '{print $2}')
- assign IAM permission
gcloud kms keyrings add-iam-policy-binding $KEYRING_NAME \
--location global \
--member user:$USER_EMAIL \
--role roles/cloudkms.admin
- assign cryptokey
gcloud kms keyrings add-iam-policy-binding $KEYRING_NAME \
--location global \
--member user:$USER_EMAIL \
--role roles/cloudkms.cryptoKeyEncrypterDecrypter
Back up data on the Command Line
gsutil -m cp -r gs://enron_emails/allen-p .
- Copy ke bucket
MYDIR=allen-p FILES=$(find $MYDIR -type f -not -name "*.encrypted") for file in $FILES; do PLAINTEXT=$(cat $file | base64 -w0) curl -v "https://cloudkms.googleapis.com/v1/projects/$DEVSHELL_PROJECT_ID/locations/global/keyRings/$KEYRING_NAME/cryptoKeys/$CRYPTOKEY_NAME:encrypt" \ -d "{\"plaintext\":\"$PLAINTEXT\"}" \ -H "Authorization:Bearer $(gcloud auth application-default print-access-token)" \ -H "Content-Type:application/json" \ | jq .ciphertext -r > $file.encrypted done gsutil -m cp allen-p/inbox/*.encrypted gs://${BUCKET_NAME}/allen-p/inbox
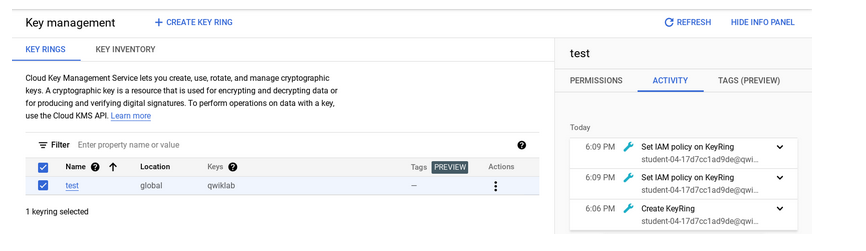
View Cloud Audit Logs
akses Navigation menu > Security > Key management
Penutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Cloud KMS. Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.
(Visited 1,159 times, 4 visits today)














