“Automating the Deployment of Networks with Terraform”
Daftar Isi
Pengantar
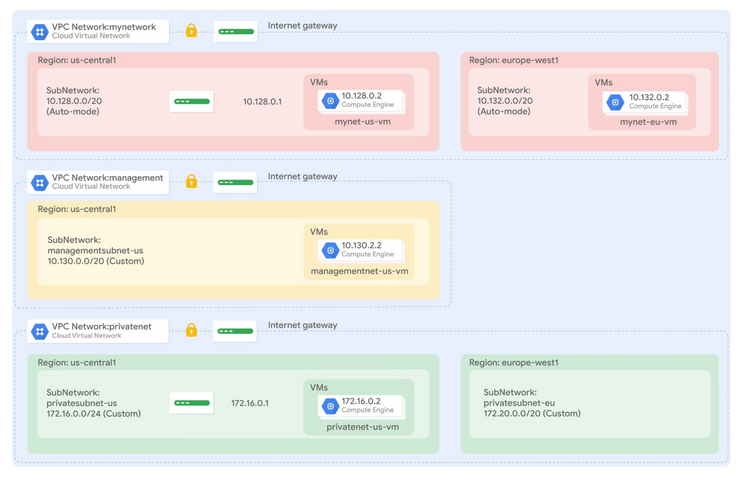
Di lab ini, Anda akan membuat konfigurasi Terraform dengan modul untuk mengotomatiskan penerapan jaringan kustom dengan resource. Secara khusus, Anda menerapkan 3 jaringan dengan aturan firewall dan instance VM, seperti yang ditampilkan dalam diagram jaringan ini:
Praktikum
Task 1. Set up Terraform and Cloud Shell
Install Terraform
- Download Terraform
wget https://releases.hashicorp.com/terraform/1.2.7/terraform_1.2.7_linux_amd64.zip- Unzip Terraform by running the following command:
unzip terraform_1.2.7_linux_amd64.zip- Set the PATH environmental variable to Terraform binaries:
export PATH="$PATH:$HOME/terraform"
cd /usr/bin
sudo ln -s $HOME/terraform
cd $HOME
source ~/.bashrc- Confirm the Terraform installation by running the following command:
terraform --version- Export the Google Cloud project into an environment variable by running the following command in Cloud Shell:
export GOOGLE_PROJECT=$(gcloud config get-value project)- Create a directory for your Terraform configuration by running the following command:
mkdir tfnet- In Cloud Shell, click Open Editor to open Cloud Shell Editor. Click Open in a new window if required.
- Expand the tfnet folder in the left pane of the code editor.
Initialize Terraform
- To create a new file in the tfnet folder, click File > New File.
- Name the new file provider.tf, and then open it.
- Copy the code into provider.tf:
provider "google" {}- Initialize Terraform by running the following commands:
cd tfnet
terraform initTask 2. Create managementnet and its resources
Configure managementnet
- To create a new file, click File > New File.
- Name the new file managementnet.tf, and then open it.
- Copy the following base code into managementnet.tf:
# Create the managementnet network
resource [RESOURCE_TYPE] "managementnet" {
name = [RESOURCE_NAME]
#RESOURCE properties go here
}- In managementnet.tf, replace
[RESOURCE_TYPE]with"google_compute_network". - In managementnet.tf, replace
[RESOURCE_NAME]with"managementnet". - Add the following property to managementnet.tf:
auto_create_subnetworks = "false"- Verify that managementnet.tf looks like this:
# Create managementnet network
resource "google_compute_network" "managementnet" {
name = "managementnet"
auto_create_subnetworks = false
}- To save managementnet.tf, click File > Save.
Add a subnet to managementnet
- Add the following resource to managementnet.tf:
# Create managementsubnet-us subnetwork
resource "google_compute_subnetwork" "managementsubnet-us" {
name = "managementsubnet-us"
region = "us-central1"
network = google_compute_network.managementnet.self_link
ip_cidr_range = "10.130.0.0/20"
}- To save managementnet.tf, click File > Save.
Configure the firewall rule
- Add the following base code to managementnet.tf:
# Add a firewall rule to allow HTTP, SSH, RDP and ICMP traffic on managementnet
resource [RESOURCE_TYPE] "managementnet-allow-http-ssh-rdp-icmp" {
name = [RESOURCE_NAME]
source_ranges = [
"0.0.0.0/0"
]
#RESOURCE properties go here
}- In managementnet.tf, replace
[RESOURCE_TYPE]with"google_compute_firewall": - In managementnet.tf, replace
[RESOURCE_NAME]with"managementnet-allow-http-ssh-rdp-icmp". - Add the following property to managementnet.tf:
network = google_compute_network.managementnet.self_link- Add the following properties to managementnet.tf:
allow {
protocol = "tcp"
ports = ["22", "80", "3389"]
}
allow {
protocol = "icmp"
}- To save managementnet.tf, click File > Save
Configure the VM instance
- To create a new folder inside tfnet, select the tfnet folder, and then click File > New Folder.
- Name the new folder instance.
- To create a new file inside instance, select the instance folder, and then click File > New File.
- Name the new file main.tf, and then open it.
- Copy the following base code into main.tf:
resource [RESOURCE_TYPE] "vm_instance" {
name = [RESOURCE_NAME]
#RESOURCE properties go here
}- in main.tf, replace
[RESOURCE_TYPE]with"google_compute_instance". - In main.tf, replace
[RESOURCE_NAME]withvar.instance_name. - Add the following properties to main.tf:
zone = var.instance_zone
machine_type = var.instance_type- Add the following properties to main.tf:
boot_disk {
initialize_params {
image = "debian-cloud/debian-11"}
}- Add the following properties to main.tf:
network_interface {
subnetwork = var.instance_subnetwork
access_config {
# Allocate a one-to-one NAT IP to the instance
}
}- Define the 4 input variables at the top of main.tf and verify that main.tf looks like this, including brackets
{}:
variable "instance_name" {}
variable "instance_zone" {}
variable "instance_type" {
default = "n1-standard-1"
}
variable "instance_subnetwork" {}
resource "google_compute_instance" "vm_instance" {
name = var.instance_name
zone = var.instance_zone
machine_type = var.instance_type
boot_disk {
initialize_params {
image = "debian-cloud/debian-11"
}
}
network_interface {
subnetwork = var.instance_subnetwork
access_config {
# Allocate a one-to-one NAT IP to the instance
}
}
}- To save main.tf, click File > Save.
- Add the following VM instance to managementnet.tf:
# Add the managementnet-us-vm instance
module "managementnet-us-vm" {
source = "./instance"
instance_name = "managementnet-us-vm"
instance_zone = "us-central1-a"
instance_subnetwork = google_compute_subnetwork.managementsubnet-us.self_link
}- To save managementnet.tf, click File > Save.
Create managementnet and its resources
- Rewrite the Terraform configurations files to a canonical format and style by running the following command:
terraform fmt
terraform init
terraform plan
terraform apply
yesVerify managementnet and its resources
- In the Cloud Console, select Navigation menu > VPC network > VPC networks.
- View the managementnet VPC network with its subnetwork.
- In the left pane, click Firewall.
- View the managementnet_allow_http_ssh_rdp_icmp firewall rule for the VPC network that was created.
- Select Navigation menu > Compute Engine > VM instances.
- Note the managementnet-us-vm instance.
- Return to Cloud Shell.
Task 3. Create privatenet and its resources
Configure privatenet
- To create a new file in the tfnet folder, click File > New File.
- Name the new file privatenet.tf, and then open it.
- Add the VPC network by copying the following code into privatenet.tf:
# Create privatenet network
resource "google_compute_network" "privatenet" {
name = "privatenet"
auto_create_subnetworks = false
}- Add the privatesubnet-us subnet resource to privatenet.tf:
# Create privatesubnet-us subnetwork
resource "google_compute_subnetwork" "privatesubnet-us" {
name = "privatesubnet-us"
region = "us-central1"
network = google_compute_network.privatenet.self_link
ip_cidr_range = "172.16.0.0/24"
}- Add the privatesubnet-eu subnet resource to privatenet.tf:
# Create privatesubnet-eu subnetwork
resource "google_compute_subnetwork" "privatesubnet-eu" {
name = "privatesubnet-eu"
region = "europe-west1"
network = google_compute_network.privatenet.self_link
ip_cidr_range = "172.20.0.0/24"
}- To save privatenet.tf, click File > Save.
Configure the firewall rule
- Add the firewall resource to privatenet.tf:
# Create a firewall rule to allow HTTP, SSH, RDP and ICMP traffic on privatenet
resource "google_compute_firewall" "privatenet-allow-http-ssh-rdp-icmp" {
name = "privatenet-allow-http-ssh-rdp-icmp"
source_ranges = [
"0.0.0.0/0"
]
network = google_compute_network.privatenet.self_link
allow {
protocol = "tcp"
ports = ["22", "80", "3389"]
}
allow {
protocol = "icmp"
}
}- To save privatenet.tf, click File > Save.
Configure the VM instance
- Add the VM instance resource to privatenet.tf:
# Add the privatenet-us-vm instance
module "privatenet-us-vm" {
source = "./instance"
instance_name = "privatenet-us-vm"
instance_zone = "us-central1-a"
instance_subnetwork = google_compute_subnetwork.privatesubnet-us.self_link
}- To save privatenet.tf, click File > Save.
Create privatenet and its resources
- Rewrite the Terraform configurations files to a canonical format and style by running the following command:
terraform fmt
terraform init
terraform plan
terraform applyVerify privatenet and its resources
- In the Cloud Console, select Navigation menu > VPC network > VPC networks.
- View the privatenet VPC network with its subnetworks.
- In the left pane, click VPC network > Firewall.
- View the privatenet_allow_http_ssh_rdp_icmp firewall rule for the VPC network that was created.
- Select Navigation menu > Compute Engine > VM instances.
- Note the internal IP addresses for privatenet-us-vm.
- For managementnet-us-vm, click SSH to launch a terminal and connect.
- To test connectivity to privatenet-us-vm‘s internal IP address, run the following command in the SSH terminal (replacing privatenet-us-vm’s internal IP address with the value noted earlier):
ping -c 3 <Enter privatenet-us-vm's internal IP here>Task 4. Create mynetwork and its resources
Configure mynetwork
- To create a new file in the tfnet folder, click File > New File.
- Name the new file mynetwork.tf, and then open it.
- Copy the following code into mynetwork.tf:
# Create the mynetwork network
resource "google_compute_network" "mynetwork" {
name = "mynetwork"
#RESOURCE properties go here
}- Add the following property to mynetwork.tf
auto_create_subnetworks = "true"- Verify that mynetwork.tf looks like this:
# Create the mynetwork network
resource "google_compute_network" "mynetwork" {
name = "mynetwork"
auto_create_subnetworks = true
}- To save mynetwork.tf, click File > Save.
Configure the firewall rule
- Add the firewall resource to mynetwork.tf:
# Create a firewall rule to allow HTTP, SSH, RDP and ICMP traffic on mynetwork
resource "google_compute_firewall" "mynetwork-allow-http-ssh-rdp-icmp" {
name = "mynetwork-allow-http-ssh-rdp-icmp"
source_ranges = [
"0.0.0.0/0"
]
network = google_compute_network.mynetwork.self_link
allow {
protocol = "tcp"
ports = ["22", "80", "3389"]
}
allow {
protocol = "icmp"
}
}- To save mynetwork.tf, click File > Save.
Configure the VM instance
- Add the following VM instances to mynetwork.tf:
# Create the mynet-us-vm instance
module "mynet-us-vm" {
source = "./instance"
instance_name = "mynet-us-vm"
instance_zone = "us-central1-a"
instance_subnetwork = google_compute_network.mynetwork.self_link
}
# Create the mynet-eu-vm" instance
module "mynet-eu-vm" {
source = "./instance"
instance_name = "mynet-eu-vm"
instance_zone = "europe-west1-d"
instance_subnetwork = google_compute_network.mynetwork.self_link
}- To save mynetwork.tf, click File > Save.
Create mynetwork and its resources
- Rewrite the Terraform configurations files to a canonical format and style by running the following command:
terraform fmt
terraform init
terraform plan
terraform applyVerify mynetwork and its resources
- In the Cloud Console, select Navigation menu > VPC network > VPC networks.
- View the mynetwork VPC network with its subnetworks.
- In the left pane, click Firewall.
- View the mynetwork-allow-http-ssh-rdp-icmp firewall rule for the VPC network that was created.
- Select Navigation menu > Compute Engine > VM instances.
- View the mynet-us-vm and mynet-eu-vm instances.
- Note the internal IP addresses for mynet-eu-vm.
- For mynet-us-vm, click SSH to launch a terminal and connect.
- To test connectivity to mynet-eu-vm‘s internal IP address, run the following command in the SSH terminal (replacing mynet-eu-vm’s internal IP address with the value noted earlier):
ping -c 3 <Enter mynet-eu-vm's internal IP here>Penutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Automating the Deployment of Networks with Terraform. Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.














