“Building a VPN Between Google Cloud and AWS with Terraform”
Daftar Isi
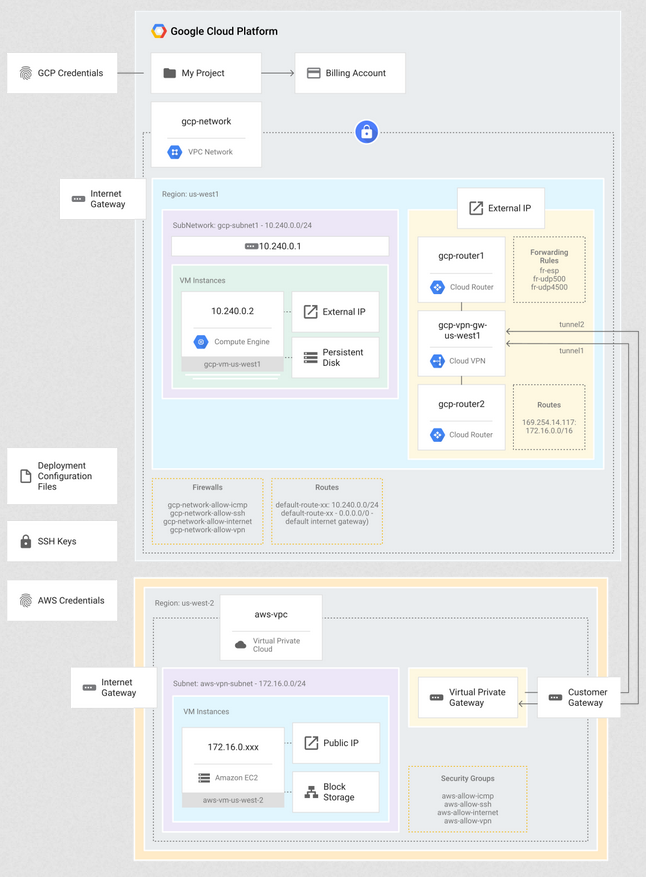
Deployment Architecture
Persiapan
Perisapan Penggunaan GCP
- Masuk ke GCP
- clone multivpn
git clone https://github.com/GoogleCloudPlatform/autonetdeploy-multicloudvpn.git
- Masuk ke folder
cd autonetdeploy-multicloudvpn
Perisapan Penggunaan AWS
- login ke dashboard AWS
- Masuk ke menu Services > Compute > EC2
- Pastikan ada di region
us-west-1( california )
Buat access credentials ( GCP )
- Masuk ke menu > click IAM & Admin > Service Accounts.
- Klik
Compute Engine default service account> klik 3 titik vertikal > di bawah Actions dan select Manage keys, dan click ADD KEY > Create new key
- Pilih JSON > klik Create
- Lalu file json akan terdownlod
- Pastikan di dalam cloud shell masih berada di folder
autonetdeploy-multicloudvpn - Klik titik 3
- Klik Upload
- Kemudian Upload JSON
- Jalankan perintah berikut
./gcp_set_credentials.sh ~/[PROJECT_ID]-[UNIQUE_ID].json
Buat AWS access credentials
- Masih di dashboard GCP
- Buat credential directory
export username=`whoami` mkdir /home/$username/.aws/ touch /home/$username/.aws/credentials_autonetdeploy
- Edit credential file
nano /home/$username/.aws/credentials_autonetdeploy
- Tambahkan file berikut
[default] aws_access_key_id=<Your AWS Access Key> aws_secret_access_key=<Your AWS Secret Key>
ganti AWS key dan AWS secret yang anda miliki
Misal setelah di masukan seperti berikut
cat /home/$username/.aws/credentials_autonetdeploy [default] aws_access_key_id=AKIA3INBXVI72ZO2Z4F4 aws_secret_access_key=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
- Setting terraform envi
export TF_VAR_aws_credentials_file_path=/home/$username/.aws/credentials_autonetdeploy
Setting Project
- Setting project di GCP
export PROJECT_ID=$(gcloud config get-value project) gcloud config set project $PROJECT_ID
- Gunakan script yang sudah tersedia
./gcp_set_project.sh
- Jalankan terraform initial
cd terraform terraform init
- Plan
terraform plan
Gunakan SSH keys untuk Koneksi ke VM instances
- Masih di GCP cloud shell -> generate new keypair -> Enter
ssh-keygen -t rsa -f ~/.ssh/vm-ssh-key -C $username
- ubah permission
chmod 400 ~/.ssh/vm-ssh-key
Import public key ke Google Cloud
- Register public key di cloud shell GCP
gcloud compute config-ssh --ssh-key-file=~/.ssh/vm-ssh-key
- Buka menu Compute Engine > Metadata
- Klik SSH Key
- nanti muncul seperti berikut
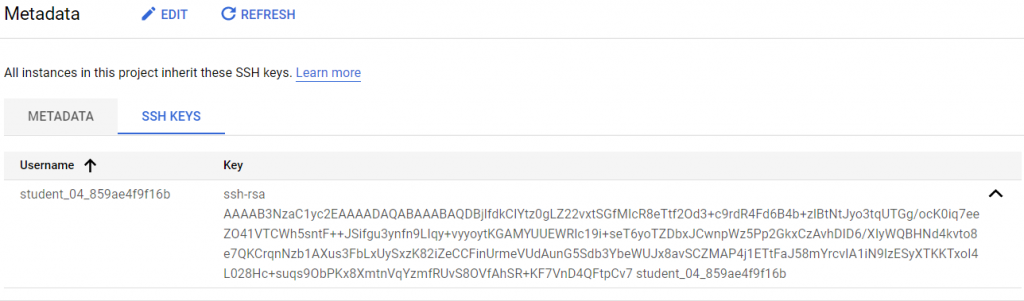
- Nanti key ini akan di import ke AWS
Import public key dari GCp ke AWS
- Login ke AWS Management Console
- Buka Services > Compute > EC2
- Pastikan ada di Region
us-west-1( California) - Scrol ke menu Network & Security -> pilih Key Pairs
- Klik Actions > Import Key Pair
- Tambahkan nama
vm-ssh-key - Masukan key yang dari GCP
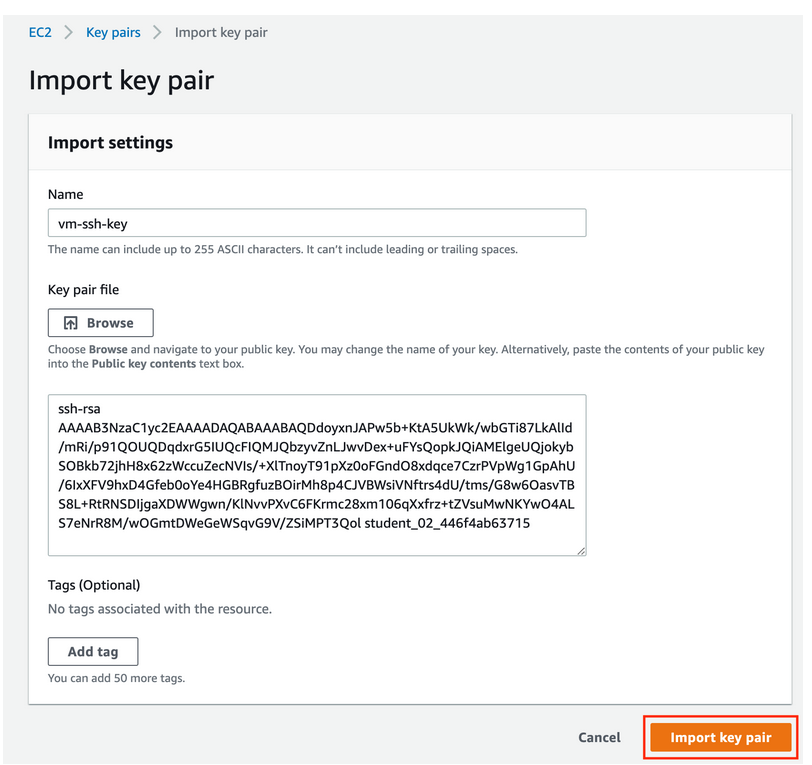
- Kemudian klik Import key pair
Deploying VPC networks, VM instances, VPN gateways, dan IPsec tunnels
Dari script yang sudah di clone , berikut yang akan di deploy
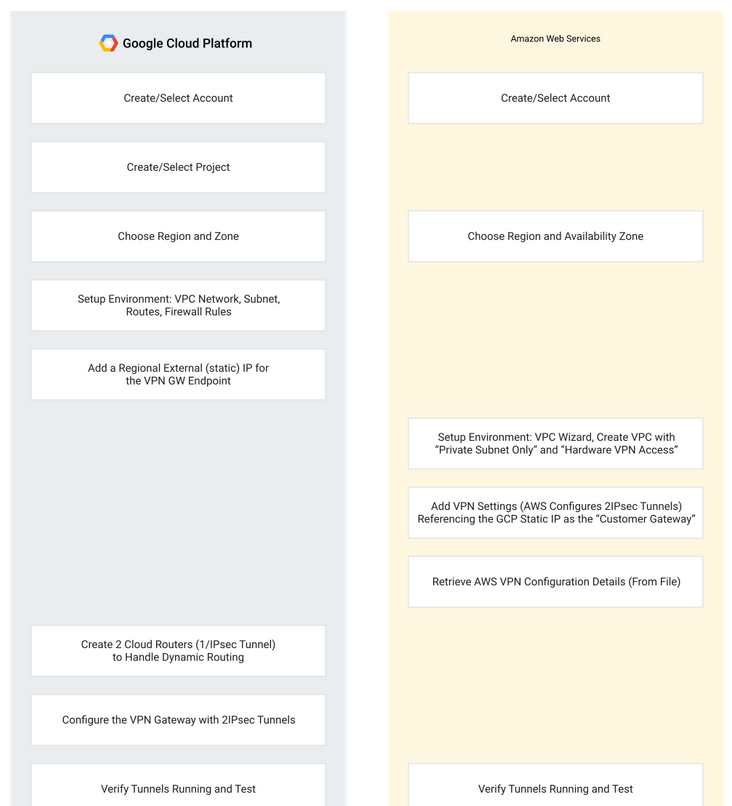
Deploy dengan Terraform
- Masuk ke cloud shell GCP
- Ubah directory
cd ~/autonetdeploy-multicloudvpn/terraform
- kemudian validate
terraform validate
- plan
terraform plan
- apply -> yes
terraform apply
- Tunggu proses nya karena proses ini akan membuat 30+ resources untuk mu, including GCP danAWS VPC networks, VM instances, VPN gateways, and IPsec tunnels.
Vm di GCP
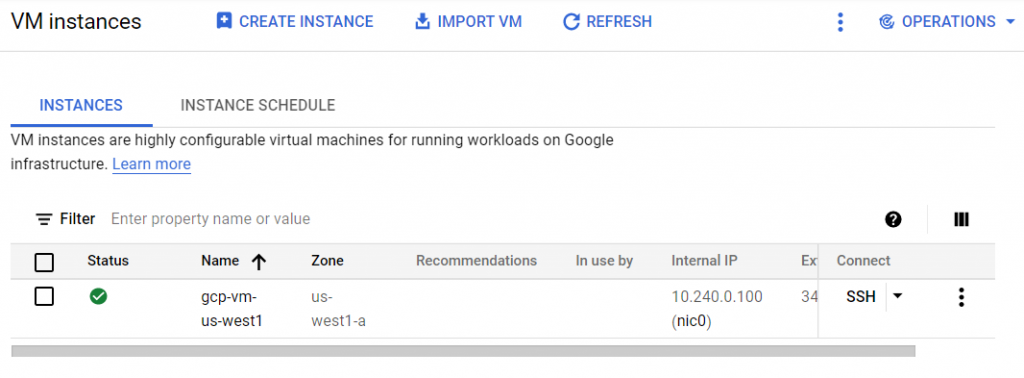
Vm di AWS
- Untuk melihat IP external di GCP dan AWS
terraform output
aws_instance_external_ip = [AWS_EXTERNAL_IP] aws_instance_internal_ip = 172.16.0.100 gcp_instance_external_ip = [GCP_EXTERNAL_IP] gcp_instance_internal_ip = 10.240.0.100
Penutup
Sahabat Blog Learning & Doing demikianlah penjelasan mengenai Building a VPN Between Google Cloud and AWS with Terraform . Semoga Bermanfaat . Sampai ketemu lagi di postingan berikut nya.
(Visited 1,205 times, 27 visits today)














